Writeup of ExtractMyBlocks
Block make us think about AES !
So when we check the given script, we can see that is actually AES - ECB
When we sent a random text in the Account Id field it returns back :
|
|
How it works
Encrypted in AES, that looks like :
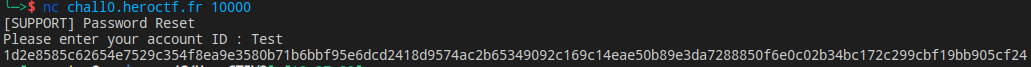
We know that the block’s size is 32 hex char. So we can cut the request in blocks like this :
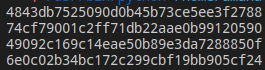
So know we can start the attack, we have to send a specific amount of char to see when a new block is created. I counted the bytes in the previous message and I found :
|
|
The attack is based on extract the chars of the flag one by one. The trick is : if we build a payload that is 13 bytes long instead of 14, there is 1 byte left, and it’s a flag byte !
The final script
Here is my script :
|
|
Launch the script and the flag pops up !
Hero{_BL0CK5_}
Thanks to the challmaker for this cool challenge !
